Researchers found another vulnerability in SpaceX’s Starlink system just 2 months after Starlink was hacked using a $25 homemade device

Early this month, the Ukrainian troops on the frontline reported ‘catastrophic’ outages of their Starlink communication devices. The connectivity issues hindered their efforts from liberating captured territory from Russian forces.
Roman Sinicyn, a co-ordinator at a foundation that donated the Starlink systems to the Ukrainian forces, told the Financial Times the outage issue was probably caused by SpaceX reps working to ensure Russian soldiers couldn’t interfere with Starlink technology.
But that has not stopped some media outlets from blaming the Russian military for the outage. Musk also tweeted: “Russia is actively trying to kill Starlink. To safeguard, SpaceX has diverted massive resources towards defense.”
Perhaps, hacking Starlink does not necessarily require the expertise of a state actor. As it turns out, there’s a vulnerability in the Starlink system that can be exploited by hackers with just a $25 homemade device.
In August, security researcher Lennert Lennert Wouters said he was able to hack into Starlink using $25 worth of off-the-shelf modchip (modification chip), a homemade circuit board that he built to hack into the Starlink system.
In a news release posted on BlackHat.com, Wouters, a researcher based out of the Belgian university KU Leuven, documented and disclosed how the attacks were performed within the scope of the SpaceX Bug Bounty program. He made the revelation during the security breakdown at a computer security conference in Las Vegas.
“The widespread availability of Starlink User Terminals (UT) exposes them to hardware hackers and opens the door for an attacker to freely explore the network,” Wouters said.
According to Wired, Wouters’ modchip was built using parts that could easily be bought off-the-shelf for around $25. To gain access to the Starlink satellite dish’s software, Wouters physically stripped down a dish he purchased and created a custom hacking tool (modchip) that can be attached to the Starlink dish.
Once attached to the Starlink dish, Wouters then used the homemade printed circuit board (PCB) to launch a fault injection attack—temporarily shorting the system—to help bypass Starlink’s security protections. “This “glitch” allows Wouters to get into previously locked parts of the Starlink system,” Wired reported.
#DishyMcFlatFace is live @defcon! Picture sent via magical space radio waves 🚀🛰️
Remember to checkout our booth tomorrow in the @rfhackers village! Can’t wait to hang out with all you humans! #DEFCON30 pic.twitter.com/WQrx3gvGW7
— Christopher Stanley (@cstanley) August 11, 2022
Unfortunately, Wouters is not alone. a team of US scientists has just discovered another vulnerability or weakness in the Starlink system during the research project to reverse-engineer Starlink signals to work like GPS and offer a precise position, navigation, and timing.
According to a report published yesterday by MIT Technology Review Magazine, Todd Humphreys of the University of Texas at Austin was able to capture the signal structure of the Starlink Ku-Band downlink. In a non-peer-reviewed paper posted on his lab’s website, Humphreys claims to have developed a technique for blind signal identification
of the Starlink downlink signal to date.
He stated that documenting the Starlink signal is the first step toward developing a new global navigation technology that would operate independently of GPS or its European, Russian, and Chinese equivalents.
“Such an understanding of the signal is essential to emerging efforts that seek to dual-purpose Starlink signals for positioning, navigation, and timing, despite their being designed solely for broadband Internet provision.
Humphreys and his team at the University of Texas at Austin’s Radionavigation Lab have been reverse-engineering signals sent from thousands of Starlink internet satellites in low Earth orbit (LEO) to ground-based receivers. After working for two years, his team finally cracked the problem.
“The Starlink system signal is a closely guarded secret,” says Humphreys. “Even in our early discussions, when SpaceX was being more cooperative, they didn’t reveal any of the signal structure to us. We had to start from scratch, building basically a little radio telescope to eavesdrop on their signals.”
To start off the project, Humphreys and his team at UT Austin acquired a Starlink terminal and used it to stream high-definition tennis videos of Rafael Nadal from YouTube. The terminal provided them with a constant source of Starlink signals that a different nearby antenna could listen in on.
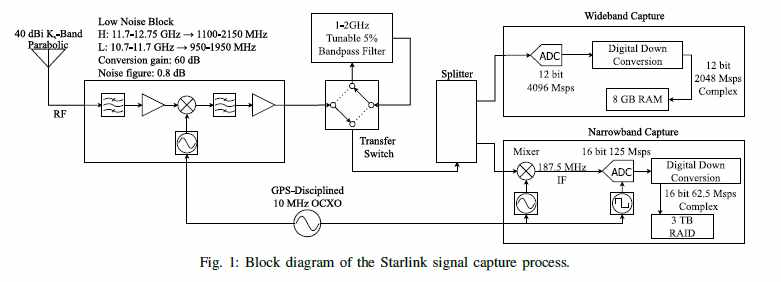
It didn’t take long for Humphreys to realize that Starlink relies on five-decade-old technology called Orthogonal frequency-division multiplexing (OFDM). Originally developed at Bell Labs in the 1960s, OFDM is an encoding digital transmission method where a single stream of data is divided into several separate sub-streams for transmission via multiple channels. It is now used in Wi-Fi and 5G.
“OFDM is all the rage. It’s a way to pack the most bits per second into a given bandwidth,” Mark Psiaki, a GPS expert and aerospace professor at Virginia Tech, told MIT Reviews.
After capturing the incoming user data from satellites, Humphreys and a team of UT Austin researchers tried to “find synchronization sequences—predictable, repeating signals beamed down by the satellites in orbit to help receivers coordinate with them.” Not only did they find such sequences, but “we were pleasantly surprised to find that they [had] more synchronization sequences than is strictly required,” Humphreys added.
That’s not all. Humphreys and his team also found that each sequence also contains clues to the satellite’s distance and velocity. With the Starlink satellites transmitting about four sequences every millisecond “that’s just wonderful for dual use of their system for positioning,” Humphreys said.
But UT Austin’s unexpected findings also highlight the danger of deliberate interference with Starlink itself by hackers. While the synchronization sequences of Starlink hold promise for navigation and positioning, the fact that they are totally predictable and are used across the whole constellation posses a security vulnerability.
“Humphreys has done a big service to the navigation community identifying these sequences,” says Psiaki. “But any navigation system working on open-source sequences could definitely be spoofed, because everyone will know how to spot those signals and create fake ones.”
Meanwhile, Humphreys and his team at UT Austin are not the only researchers exploring the use of Starlink as GPS. In 2021, Zak Kassas, a professor in the department of Electrical and Computer Engineering at Ohio State University, and his team were the first to demonstrate that Starlink signals could be used for positioning.
Unlike the UT Austin team, Kassas used an approach called cognitive opportunistic navigation, which analyzes the period and changing frequencies of signals from a satellite as it travels overhead. But their receiver also uses the synchronization sequences, learns the satellite’s orbit, and tracks it.
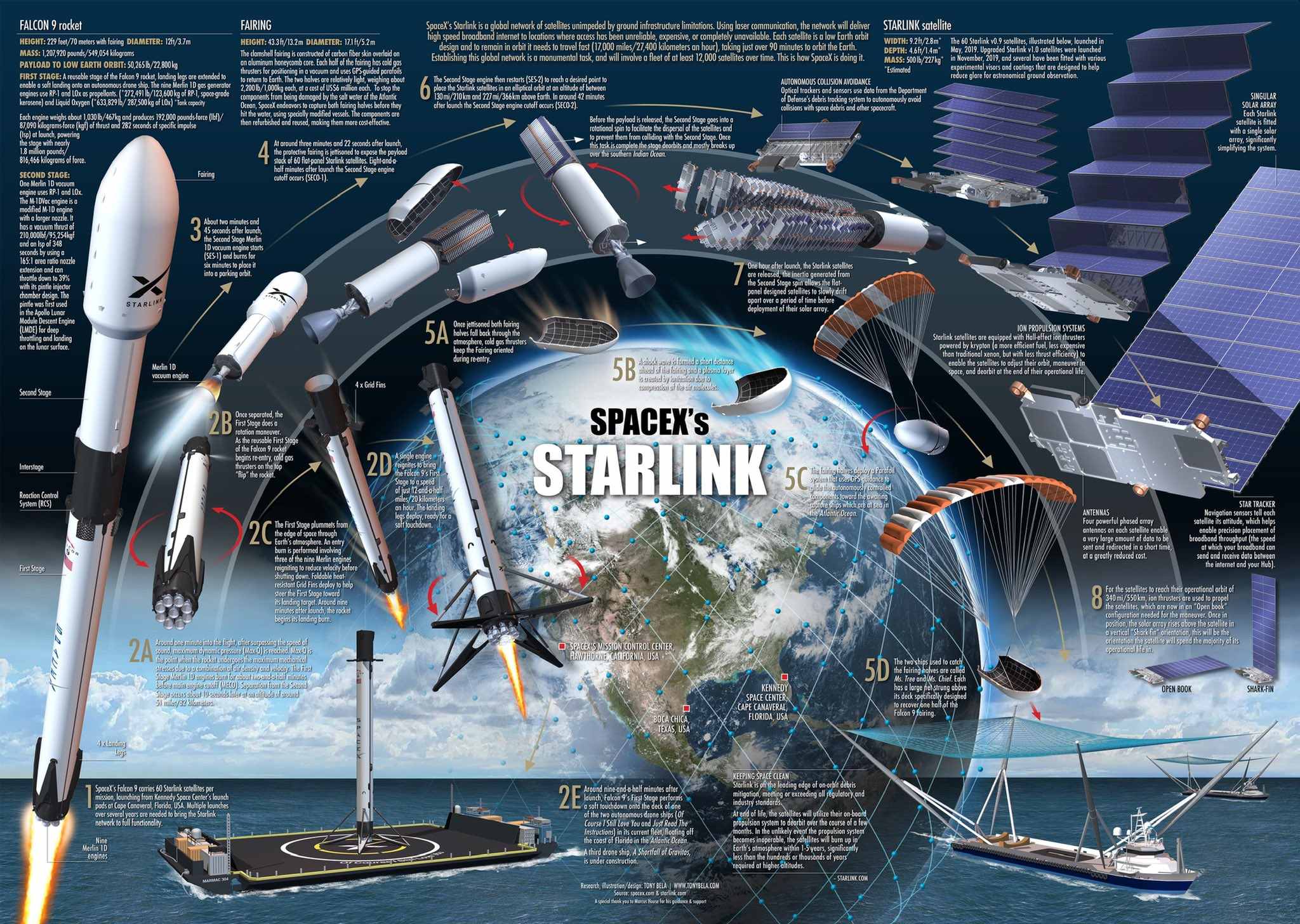
Starlink is a satellite internet constellation that provides satellite Internet access. According to SpaceX, the constellation will consist of thousands of mass-produced small satellites in low Earth orbit (LEO), working in combination with ground transceivers. SpaceX also plans to sell some of the satellites for the military, scientific, or exploratory purposes.
starlink-structure