Salus’ Research on Using Deep Learning to Detect Smart Contract Vulnerability Published in Scientific Reports, a sub-journal of Nature

Salus, a prominent blockchain security startup, has gained recognition after its research was featured in the Scientific Reports section of the prestigious Nature Magazine. The study explores the use of deep learning to identify vulnerabilities in smart contracts, representing a noteworthy advancement for web3. The acknowledgment from a sub-journal of Nature lends considerable credibility to the research, underscoring the significance of the findings from a reputable scientific source.
The research paper investigates the crucial role of smart contracts in blockchain technology and the potential financial losses and system failures resulting from vulnerabilities in these contracts. It sheds light on the challenges associated with existing methods, particularly the limitations of static analysis tools, which often yield false positives and negatives due to their reliance on predefined rules.
Introduction
Ever since Satoshi Nakamoto reintroduced blockchain more than two decades ago, it has served as the underline technology for many decentralized applications, including cryptocurrencies. Beyond that, it stands out as an inventive application pattern built on technologies such as point-to-point transmission, encryption algorithms, consensus mechanisms, and distributed data storage.
With the advent of Bitcoin, the foundational blockchain system has also gained significant recognition, leading to the creation of various blockchain applications. Smart contracts play a pivotal role in this ecosystem. They are automated programs that operate within the secure environment of the blockchain. However, if vulnerabilities exist in smart contracts deployed on the blockchain, attackers can exploit these weaknesses to carry out malicious attacks.
The research cited several historical incidents to exemplify the repercussions of such vulnerabilities, including one notable incident that occurred on June 17, 2016, when The DAO, the largest crowdfunding project in the blockchain industry at that time, fell victim to an attack. Exploiting a reentrancy vulnerability, the attacker managed to steal 3.6 million Ether, equivalent to around $60 million. This incident resulted in a significant split in the Ethereum blockchain into ETH (Ethereum) and ETC (Ethereum Classic). Subsequent examples include attacks on the BEC smart contract in 2018 and the bZx protocol in 2020, each exploiting vulnerabilities and causing disruptions in the blockchain ecosystem.
The common thread in these incidents is the substantial financial losses and disruptions caused by attackers manipulating vulnerabilities in smart contracts. This highlights the critical need for early detection and mitigation of vulnerabilities in smart contracts to ensure the security of assets and protect against potential theft or other security risks.
The research paper underscores the importance of conducting vulnerability detection on smart contracts as an essential practice in the development and deployment processes. Detecting vulnerabilities early on can prevent unforeseen asset losses, contribute to overall security, and uphold user trust. It positions smart contract vulnerability detection as a crucial element in safeguarding the integrity of blockchain applications, preventing financial losses, and maintaining the trust of users involved in the blockchain ecosystem. Ultimately, the narrative emphasizes the overarching role of smart contract security in the broader landscape of blockchain technology.
Current Methods and Challenges
The current methods for identifying vulnerabilities in smart contracts involve human review, static analysis, fuzz testing, and formal verification. Many rely on static analysis tools like Oyente, Mythril, Securify, Slither, and Smartcheck to detect vulnerabilities in smart contracts.
These tools automatically examine contract code, addressing common security issues such as reentrancy, incorrect tx.origin authorization, timestamp dependency, and unhandled exceptions. However, their dependence on predefined rules makes them prone to generating false positives and false negatives, and they lack the capability to conduct semantic analysis. Additionally, these predefined rules swiftly become outdated, struggling to keep pace with the dynamic nature of smart contract development.
Despite their widespread use for identifying smart contract vulnerabilities, static analysis tools face challenges such as inaccuracies and an inability to adapt to the constantly evolving data landscape in smart contract development.
Salus’ Breakthrough Solutions
To address the challenges associated with the current approach, Salus came up with a groundbreaking solution – Deep Learning-Powered methods that avoid predefined detection rules, and learning vulnerability features during the training process. The research paper introduces “Lightning Cat,” a solution based on deep learning techniques, with three trained models: Optimized-CodeBERT, Optimized-LSTM, and Optimized-CNN. These models aim to overcome the shortcomings of static analysis tools by adapting to evolving data without the need for predefined rules.
For data preprocessing, the research paper employs CodeBERT for accurate capture of code syntax and semantics, focusing on extracting vulnerability features from segments of vulnerable code functions. The experimental results showcase the effectiveness of Lightning Cat, especially the Optimized-CodeBERT model, which outperforms other methods with an impressive f1-score of 93.53%, a recall rate of 93.55%, and a precision rate of 96.77%.
The diagram below breaks down the entire process of creating a vulnerability detection model named Lightning Cat for smart contracts, covering three key stages. First off, there’s the initial stage where Salus blockchain researchers Xueyan Tang, Yuying Du, Alan Lai, Ze Zhang, and Lingzhi Shi, construct and preprocess a labeled dataset containing vulnerable Solidity code. Moving on to the second stage, they train three distinct models — Optimized-CodeBERT, Optimized-LSTM, and Optimized-CNN — and then compare their performances to identify the most effective one. Lastly, in the third stage, researchers assess the selected model’s effectiveness in detecting vulnerabilities by evaluating it with the Sodifi-benchmark dataset.
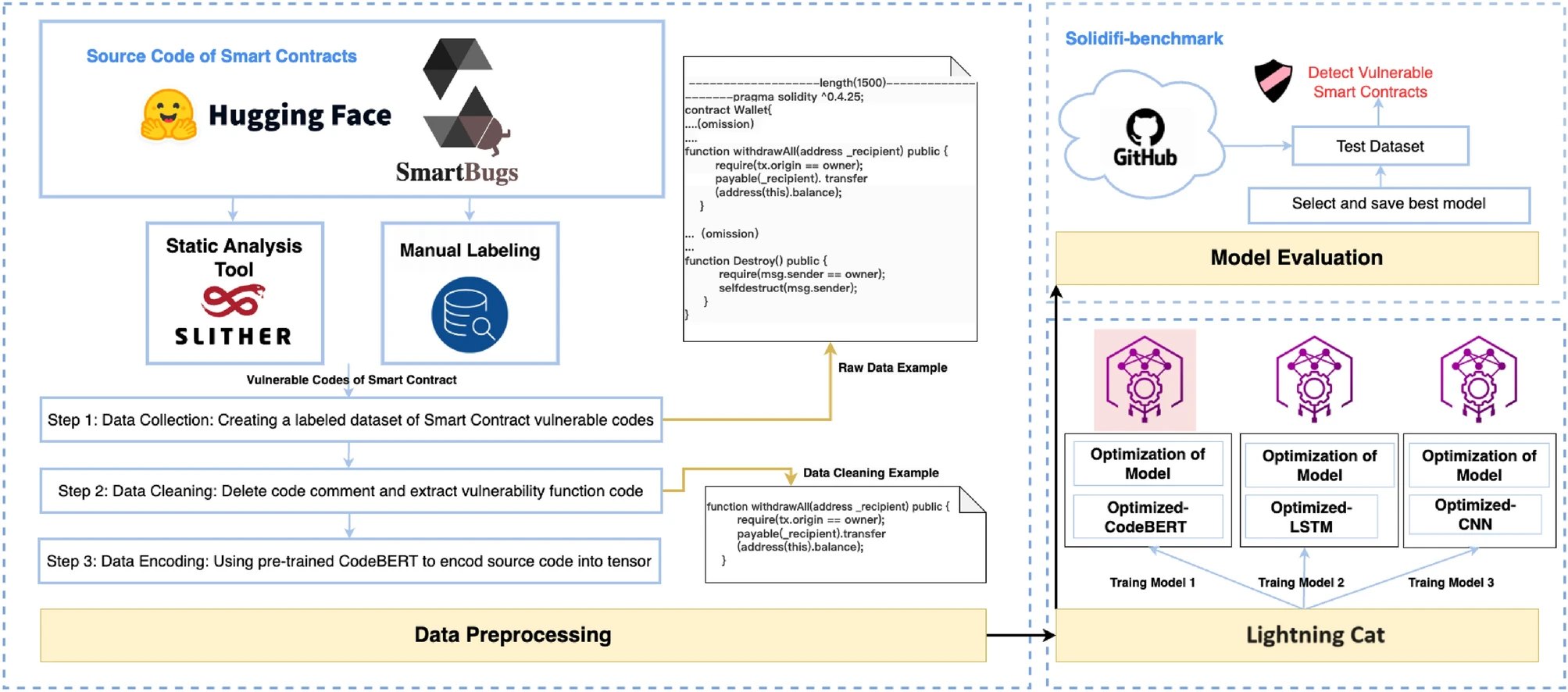
Lightning Cat Model Development Process.
Conclusion
The research concludes by establishing Lightning Cat as a potent deep learning-based solution for smart contract vulnerability detection. Emphasizing semantic analysis and adaptability, the proposed approach demonstrates promising results in enhancing security and reliability within the realm of blockchain technology. For those interested, the full research can be accessed on Nature Magazine’s website or downloaded for further reading.
You can read the full research at Nature Magazine’s website or download a copy here.

