The Three-Step Process of Security Validation to Optimize Cyber Defenses

A reliable security posture does not end with the installation of security defense systems. Cybersecurity has to be a continuing process to make sense. Cyber attacks ceaselessly evolve, as bad actors relentlessly find new ways to breach security defenses. There is no such thing as an install-and-forget solution.
For a cybersecurity system to effectively detect and block attacks, security validation is a must. After putting security controls in place, it is a must to have them tested to determine if they indeed work as intended. If weaknesses are found, tweaks and adjustments must be enacted. Sometimes, it may be necessary to replace the entire security system after poor testing results.
Cymulate, a security firm that specializes in continuous security validation, developed a three-step process for effective security testing. It’s a simple but highly efficient process that starts with simulation, followed by evaluation, then remediation.
Step 1: Simulate
How do security teams know if the security controls they put in place are working? Certainly, they do not wait for attacks to come and check if the defenses hold up. Doing so is arguably the worst way to undertake security validation.
In lieu of an actual cyber attack, what security professionals do is simulate the exploitation of potential vulnerabilities, hacks, and other activities of bad actors to find out how well the security controls stack up.
The simulation process can be conducted in many ways. In the case of Cymulate, it is an end-to-end process that starts with the reconnaissance work and advances through the simulation of email and web attacks, phishing, attempts to penetrate the supply chain, distribution of ransomware and other malware, and other campaigns to breach the fully cyber kill-chain.
These attacks can be undertaken manually or in concert with automated simulations developed by an in-house or third-party team. To more efficiently oversee the process, it helps to coordinate activities through a customizable open framework that can serve as a comprehensive repository of executed simulations and the corresponding assessments, similar to what Cymulate offers.
Cymulate makes the process easier to follow by providing comprehensive information about the security controls of an organization. Its purple team dashboard, for instance, shows a similarity analysis along with prevention and detection details.
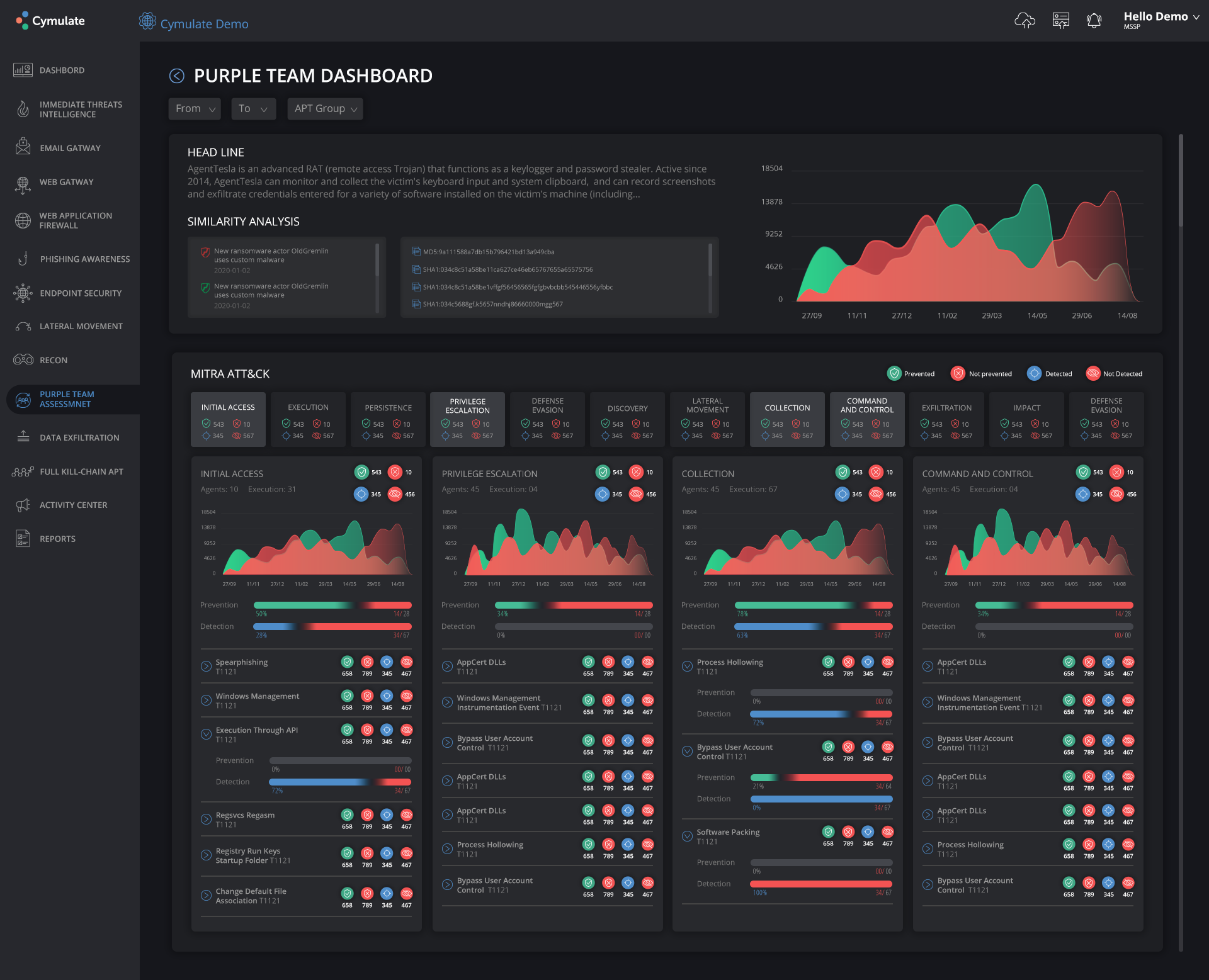
Cymulate’s Purple Team dashboard
It is understandable why some tend to be skeptical about cyber-attack simulations. There are those who would question the proficiency of those who formulate the threat scenarios. However, there is no question that attack simulations make sense.
“Simulations are useful as components of network security software and in training exercises for security professionals, as well as software aids designed for network users. Much of the basic research in cyber-related human factors and cyber epidemiology benefits from simulation software,” writes a cybersecurity simulation research paper prepared by security and cognitive science experts from various institutions.
Step 2: Evaluate
Once the simulations are completed, it’s time to proceed with the thorough scrutiny of the outcomes. This is the point where a security team gains immediate visibility into the entire network.
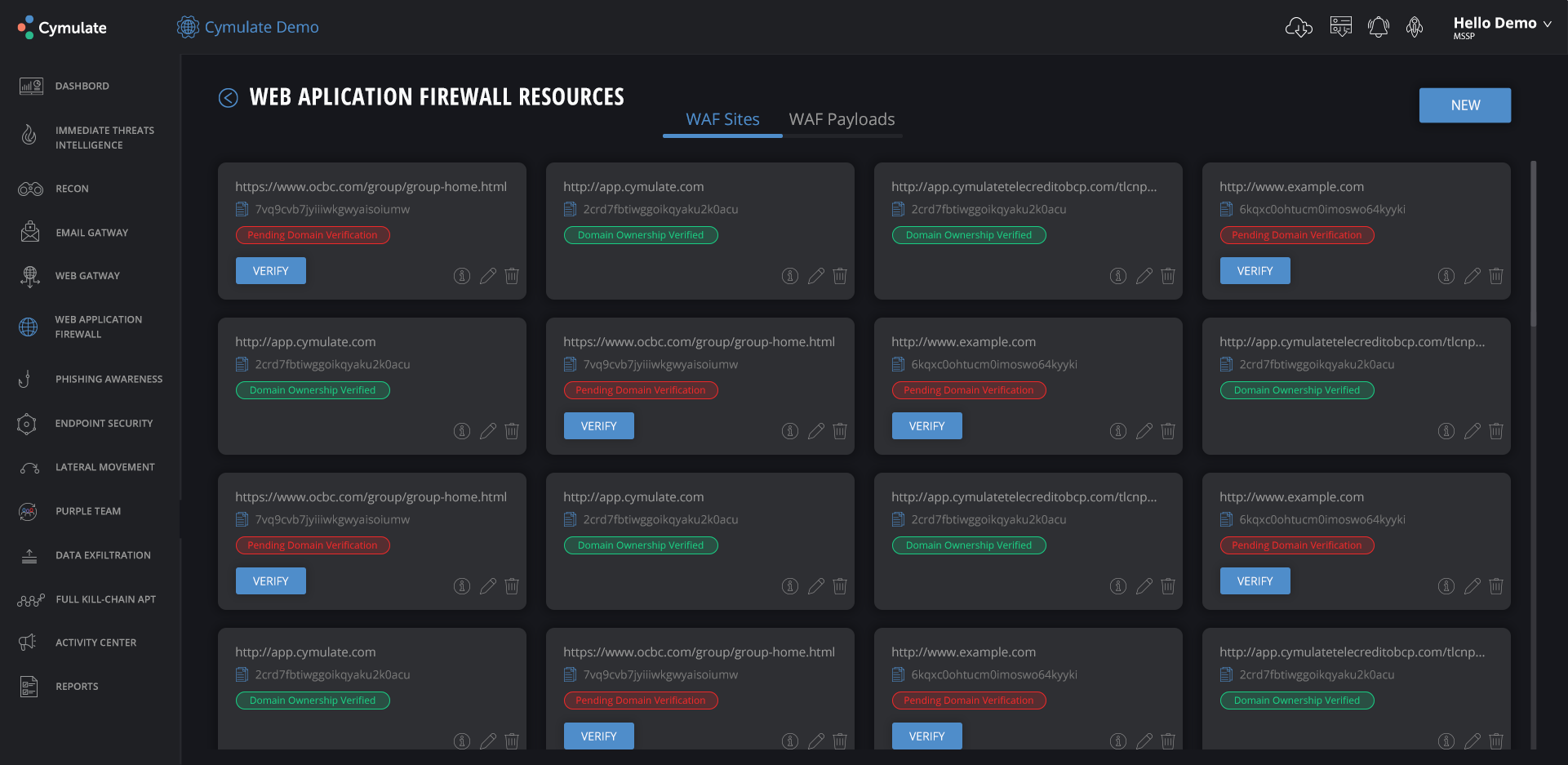
Cymulate’s WAF resource overview, an example of the enhanced security visibility that they offer
The evaluation step informs or generates insights about the current threat exposure of a network. It reveals the presence of potentially exploitable vulnerabilities including mistaken or inappropriate configurations, un-updated software, and other gaps in the security posture.
Enhanced security visibility is a must especially when a new cyber environment is established following an organizational change, which happens after a merger or acquisition for example. It can also be brought about by the replacement of enterprise hardware and software, digital transformation initiatives, and news of newly discovered threats.
Cymulate offers a platform that makes it easy to measure and monitor security performance. It generates risk scores based on established evaluation methods. These include the powerful Microsoft DREAD risks assessment model, the guidelines set forth by the National Institute of Standards and Technology (NIST), and the Common Vulnerability Scoring System (CVSS).
Aside from the risk scores, full reports and histories for the different evaluation categories are likewise supplied. Charts and graphs are shown to visualize the integrity of the security team’s existing defenses along with corresponding benchmarks for specific performance points.
To further improve the ability of organizations to evaluate the effectiveness of their cybersecurity defenses, it greatly helps to integrate the MITRE ATT&CK framework. This cybersecurity framework serves as a global resource for the latest information about adversary tactics and techniques as observed in real-world cyber attacks and the threat intelligence contributed by renowned cybersecurity-related institutions and professionals.
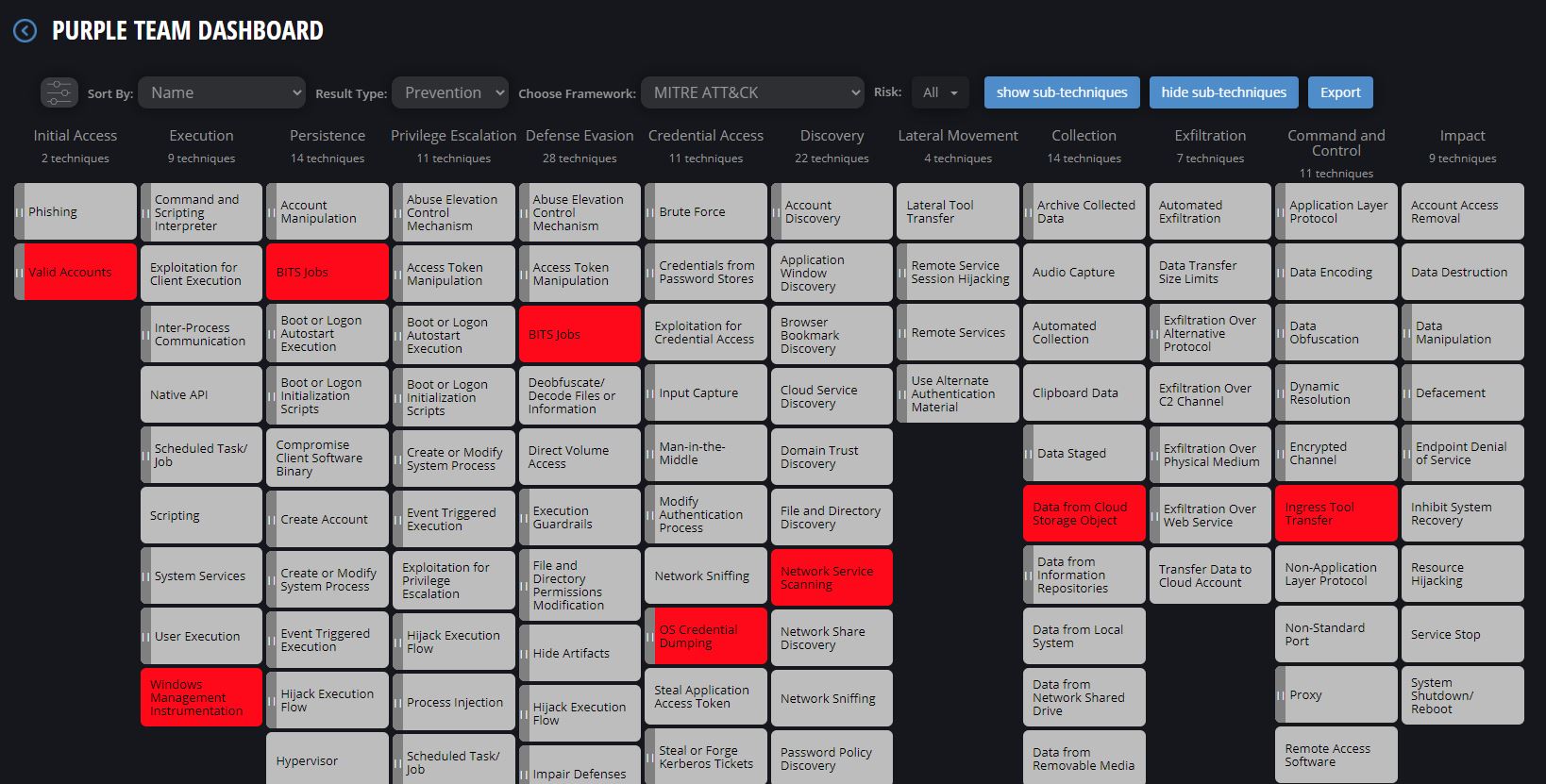
The Cymulate MITRE ATT&CK interface
Many security validation platforms already integrate MITRE ATT&CK into their systems to take advantage of the free and authoritative cyber threat information. It benefits both blue and red teams and even purple teams, as it helps anyone get acquainted with the threats posed by adversaries. It facilitates the detection and tracking of an attack, the deciphering of patterns of anomalous network activities, and the prioritization of threats to make sure that correct solutions are promptly implemented.
Step 3: Remediate
Of course, security validation does not end with the evaluation. Knowing what works and what does not, is only half the job. The most important step is the actions to be taken to address the weaknesses and further the strengths.
Security analysts can formulate courses of action after going over the results of the evaluation stage. These include the reconfiguration of certain controls, software updates, installation of more security tools, and various other solutions.
Remediation can be made easier and faster without compromising on the effectiveness with the help of a dependable security validation platform. Cymulate, for example, readily presents recommendations on what needs to be done to plug the security gaps and vulnerabilities discovered after the simulation and evaluation phases.
Cymulate’s Data Exfiltration Assessment feature tests the reliability of an organization’s Data Loss Prevention (DLP) controls and provides actionable remediation and optimization guidance. It generates a comprehensive report after every assessment and compares the results to previous tests to identify security inadequacies that require attention.
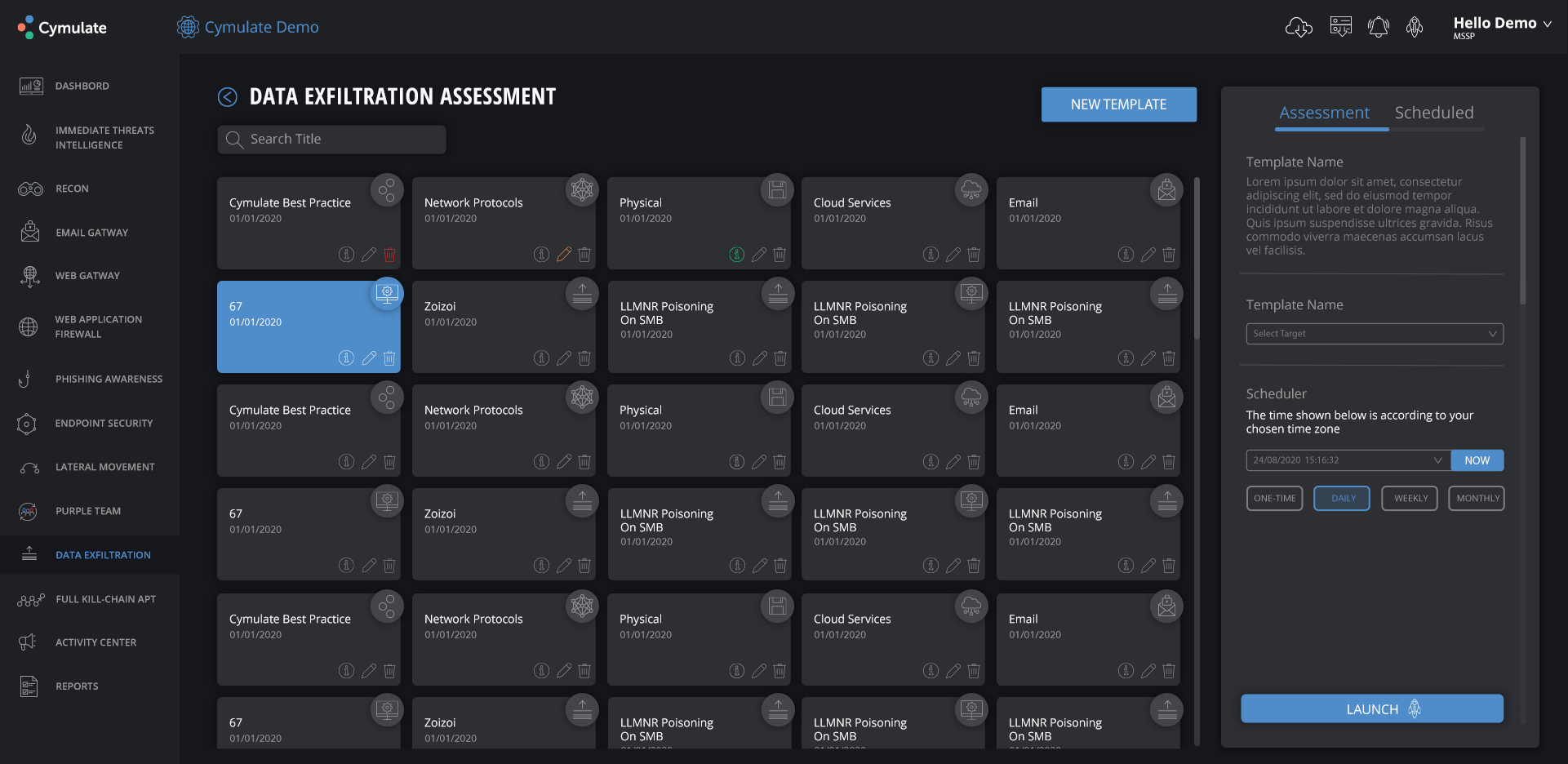
Cymulate’s Data Exfiltration Assessment interface
Cymulate shows details on the attack type, the date the attack happened, penetration ratio, and the number of files exposed to the risk, among others. The platform also indicates the level of risk of every threat discovered. This is important as it helps security teams in prioritizing resources and remediate efforts to make sure that the most critical concerns are addressed first.
It is not unusual to discover thousands of threats through automated and AI-powered attack simulations. Going over each and every threat is not only time-consuming and exhausting; it is also highly inefficient. Not all threats share the same gravity. Some need more urgent responses than others. Delayed action on some crucial issues can lead to more attacks or the facilitation of the penetration of other attacks.
It is greatly beneficial to have a way to automatically assess threats and classify them according to their risk level, so the limited remediation resources can be directed to where they are needed the most.
In summary
Simulate, evaluate, and remediate–these are simple steps that can be enough to establish a reliable security validation process. They become even more effective under a continuous security testing regime. However, no system or method is foolproof, so it is vital to pay attention to all details in every step and make use of the best cybersecurity tools.

