Pray.com, a popular Christian faith app, exposed millions of people to fraud and online attack

Just last week, we wrote about Facebook after the research team at VPNMentor found that a data breach exposed massive phishing and credit card fraud operation targeting 100,000s Facebook users. Now, VPNMentor is reporting another major data breach, this time, the breach was found on Pray.com, a popular Christian faith app that touted itself as the world’s #1 app for daily prayer and biblical audio content.”
Led by Noam Rotem and Ran Locar, the vpnMentor’s research team discovered that the Christian faith app, Pray.com, has been leaking years’ of private data collected from users. According to the team’s findings, Pray.com’s developers failed to properly secure vast amounts of data collected from the app, potentially exposing millions of people to fraud and online attacks. The VPNMentor research team said:
“In fact, most people exposed in Pray.com’s data breach don’t even use the app.”
The team published a report regarding discovered four misconfigured Amazon Web Services (AWS) S3 buckets and quickly identified Pray.com as their owner. AWS S3 buckets are a popular cloud storage solution for many apps and websites, but users must set their own security protocols. One of the four buckets contained sensitive information, such as personal identifiable information (PII) of their users (and millions of people who aren’t) other files stored in the buckets included technical details regarding their app and site, as well as marketing materials.
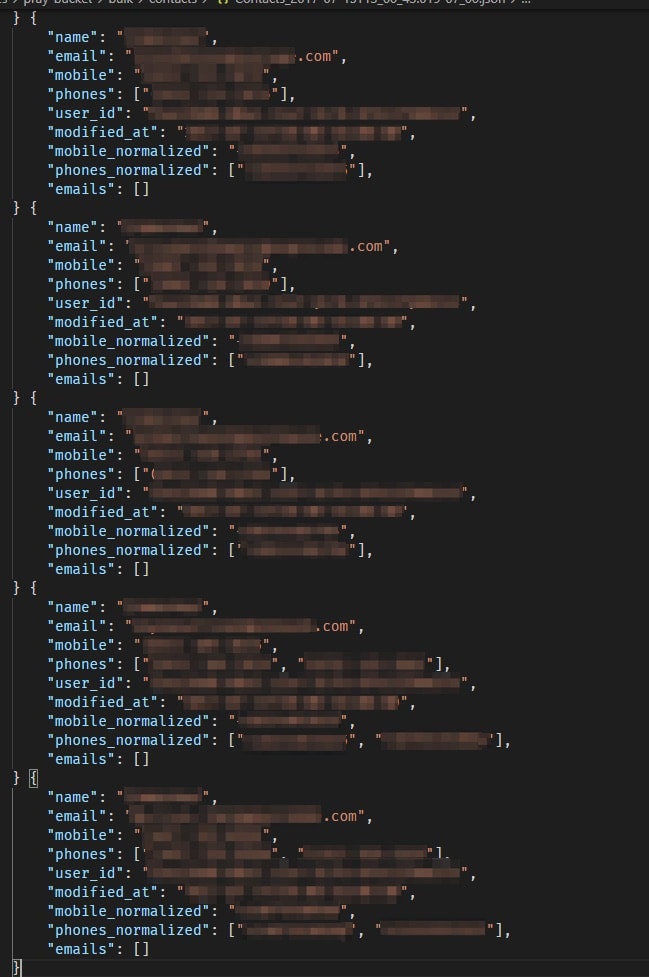
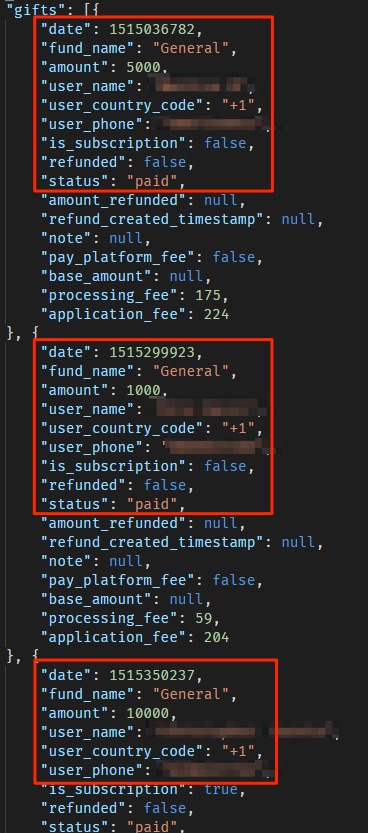
The sensitive information mentioned above consisted of detailed lists of donations, including the donor’s name, amount donated, email, and more. We also found detailed lists of Church congregations (with full name, phone number, marital status, and more); as well as over 80,000 JSON files containing users’ phonebook contacts (each from 10 to hundreds of contacts, totalizing a few million people) to which users had given access to the company when using the app.
VPNMentor said it discovered the issue on October 6, 2020, and later reported the issue to Pray.com the following day.
“Pray.com’s developers overlooked basic security protocols on the S3 buckets, leaving many of the files stored within them publicly accessible to anyone with access to the bucket’s URL (easily obtained). Through further investigation, we learned that Pray.com had protected some files, setting them as private on the buckets to limit access.”
VPNMentior added:
However, at the same time, Pray.com had integrated its S3 buckets with another AWS service, the AWS CloudFront content delivery network (CDN). Cloudfront allows app developers to cache content on proxy servers hosted by AWS around the world – and closer to an app’s users – rather than load those files from the app’s servers.
Doing so speeds up the app’s performance considerably. Pray.com seemingly overlooked installing proper security measures on its CloudFront account. As a result, any files on the S3 buckets could be indirectly viewed and accessed through the CDN, regardless of their individual security settings.
Pray.com’s developers accidentally created a backdoor that gave complete access to all the files they had tried to protect. Once we confirmed all the details of the breach, we reached out to Pray.com and presented our findings.
After our first two attempts at contacting Pray.com failed to elicit a reply, we contacted AWS directly to notify them. AWS confirmed they had informed Pray.com of the breach a few days later, but there remains no evidence that the company has attempted to resolve the issue.
Five weeks after our initial attempt to contact Pray.com, the buckets remained unsecured, but the contacts files were removed. On November 17th, after three attempts by us to reach out to Pray.com, we finally received an answer from Pray.com’s CEO. His email contained one word: “Unsubscribe”.
You can read the entire data breach report at VPNMentor.com