How Industrial Systems Have Become Prime Targets for APTs

Today, cyberwarfare has become a new front that nations in conflict have to face. Hackers have now even become the new soldiers of fortune. They now operate as advanced persistent threats (APTs) which infiltrate and lurk within vulnerable infrastructure performing various malicious activities silently. They have even organized themselves into groups in order to increase their attack capabilities.
Nations are even reported to been sponsoring APT groups to do their bidding. China, Russia, North Korea, and Iran have all been linked to attacks launched by APT groups. Recent APT activities even indicate that they are actively targeting industries and enterprises alongside government and military targets.
Nations in conflict would often seek to weaken their rivals. Cyberwarfare allows these nations to launch clandestine attacks without resorting to physical military force and directly risking the lives of their agents. And, by engaging APTs, they can even have plausible deniability for attacks.
Industries as Targets
Industrial facilities have become prime targets for state-sponsored attacks by APTs mainly because of the impact that successful attacks can have and the ease by which hackers can gain access to these systems. Taking down a single industrial target can cause major disruption to human activity. Many such facilities can also now be hacked remotely.
As cybersecurity firm odix CEO Dr. Oren Eytan points out, industrial organizations are increasingly becoming more connected as they integrate cloud-based solutions and Internet-of-Things (IoT) devices into their respective infrastructure. This growing digitization of industrial facilities and their control systems have even made them more enticing to APTs. Industries are now adopting cloud computing to augment or replace conventional on-premises servers and appliances.
Smart devices, robots, and sensors connected to the IoT are now also being installed in facilities. However, each of these components and devices are potential points of access for hackers. It only takes one vulnerable component an APT to gain access to their systems.
Protection Is a Must
Because of the potential impact of such attacks, industries must put in place more stringent cybersecurity measures and commit to best practices. They can:
Protect against modern threats. The complexity of enterprise IT infrastructure demands solutions that comprehensively protect multiple potential attack vectors against existing and emerging threats.
odix, for example, uses content disarm and reconstruction (CDR) as an approach to dealing with malware. Modern malware can feature polymorphic code and mutate on demand, rendering traditional signature and heuristic-based antivirus solutions incapable of detecting and removing them.
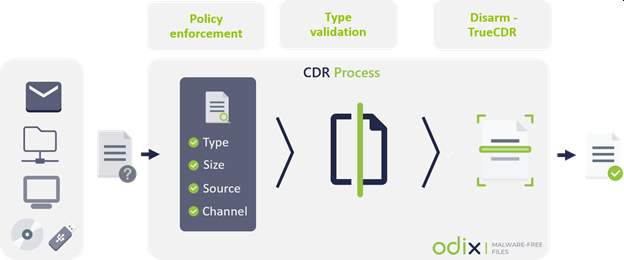
CDR can deeply scan files for all traces of malicious code and remove them while leaving the infected file still usable. odix offers tools to deploy CDR in common malware vectors such as in email servers and during file transfers and downloads. It also has an API that allows integration with enterprise software.
Use solutions to cover specialized use cases. Industrial organizations should also consider their unique circumstances when looking for solutions to adopt. Some layers may be computerized but are intentionally kept air-gapped to prevent network-based attacks. These devices may continue to be vulnerable to malware stored in removable drives and other storage devices. odix has a kiosk solution that runs as a dedicated workstation that disarms malware and sanitizes files on removable storage devices so that these can be safely used in critical air-gapped machines.
Secure devices, accounts, and endpoints. Cloud and IoT adoption may make industries more effective, but they also expand the potential attack surface for APTs. This is why it’s critical to implement capable solutions. odix’s ecosystem, for instance, is designed to cover multiple vectors and deploy CDR across an organization’s infrastructure. By protecting the routes that malware can make its way through the network such as servers, file transfers, enterprise apps and removable storage, the spread and damage malware can inflict is minimized if not handily prevented.
Organizations must also that any additional component they deploy has essential security features such as account and access management that can help thwart common methods used by APTs to gain entry into their systems.
Train human resources. Hackers may not be able to directly access some of the critical layers of industrial systems remotely so they have to rely on social engineering attacks like phishing and manipulation to force staff members located within facilities to cause security incidents. Industries can prevent these by educating and training people to identify phishing attacks and similar attempts at social engineering.
APTs Are Capable
Organizations must build capable defensive perimeters since APTs have demonstrated that they are capable of breaching poorly secured systems. Past attacks have shown how industrial systems can be vulnerable. Stuxnet, a malware allegedly developed by the US and Israel, targeted industrial control systems (ICS) and was used to effectively cripple Iran’s nuclear program back in 2010. It also affected other industrial machines globally.
The Stuxnet attacks arguably prompted Iran to increase its cyberwarfare capabilities, ushering in counterstrikes against various US targets including DDoS attacks on major banks in 2012 and 2013, and a successful hack on a New York dam in 2013. Today, Iran is regarded as a highly capable in cyberwarfare and active APT sponsor. Recently, the Iran-sponsored APT group APT33 was reported to be password-spraying industrial control systems in hopes of gaining access to various facilities.
In 2017, the Triton malware was reported to have infected several ICS in Middle Eastern oil and gas facilities, disabling fail-safe protocols that are designed to protect human life. Attacks on power grids are also among the most-feared industrial cyberattack scenarios. The successful attacks on Ukraine’s power grid in 2016 proved that it’s possible for APTs to cause actual blackouts.
As such, industrial facilities must make the necessary security investments to prevent future attacks.
“Due to the potential effects of such attacks, industrial companies need to apply the highest levels of security. It’s a good thing that standards and regulations are now being set to promote security in the sector. In the US, energy companies are required to meet the NERC CIP standards. We, at odix, understand these requirements and have helped companies in the US such as Vistra Energy and Dominion Energy achieve compliance,” says Eytan.
Conclusion
Cyberattacks on industrial facilities can truly have a major impact on any country. So, the ability of APTs to compromise such facilities gives them the clout to attract the patronage of state-sponsors. APTs have also grown more rampant due to the growing connectivity of industrial IT.
As such, it then becomes important for all industrial organizations and enterprises to strengthen their cybersecurity posture. Fortunately, there are now a variety of approaches and capable solutions that they can implement to secure their infrastructure and avoid becoming victims of APT-driven attacks down the line.
Considering how active some nations are in their cyberwarfare activities, improving their respective organizations’ defenses essentially contribute to national security.

