Google Plus is officially shutting down after security breach exposes up to 500,000 users’ data

After several attempts to compete with Facebook, Google Plus is finally shutting down. Google is shutting down the struggling social media following the discovery of a software glitch this past spring that may have exposed the private profile data of 500,000 customers between 20015 and 2018 Google+ users to outside developers.
The breach went on for about three years, according to a report from Wall Street Journal, but Google decided not to make it public because it feared regulation, and has no evidence that the bug was exploited. In response to the security incident, Google announced it’s shutting down the consumer version of Google+ by the end of August 2019.
Launched in 2011, Google+ is the company’s fourth attempt into social networking, following Google Buzz (launched 2010, retired in 2011), Google Friend Connect (launched 2008, retired by March 1, 2012), and Orkut (launched in 2004, as of 2013 operated entirely by subsidiary Google Brazil – retired in September 2014.
The company cited two reasons: low user engagement and difficulties in “creating and maintaining a successful Google+ that meets consumers’ expectations.” The company noted that 90 percent of user sessions on the service last under five seconds. It also acknowledged a design flaw in an API that potentially exposed private user data. Google said it found no evidence that “any developer was aware of this bug, or abusing the API” nor that “any Profile data was misused.”
According to the Wall Street Journal, the data exposure was discovered in the spring of 2018 but not reported by the company due to fears of increased regulatory scrutiny. The newspaper said that “the move effectively puts the final nail in the coffin of a product that was launched in 2011 to challenge Facebook Inc. and is widely seen as one of Google’s biggest failures.” In a blog post posted immediately WSJ‘s report, Google said:
“At the beginning of this year, we started an effort called Project Strobe—a root-and-branch review of third-party developer access to Google account and Android device data and of our philosophy around apps’ data access. This project looked at the operation of our privacy controls, platforms where users were not engaging with our APIs because of concerns around data privacy, areas where developers may have been granted overly broad access, and other areas in which our policies should be tightened.
We’re announcing the first four findings and actions from this review today.
Finding 1: There are significant challenges in creating and maintaining a successful Google+ product that meets consumers’ expectations.
Action 1: We are shutting down Google+ for consumers.
Over the years we’ve received feedback that people want to better understand how to control the data they choose to share with apps on Google+. So as part of Project Strobe, one of our first priorities was to closely review all the APIs associated with Google+.
This review crystallized what we’ve known for a while: that while our engineering teams have put a lot of effort and dedication into building Google+ over the years, it has not achieved broad consumer or developer adoption, and has seen limited user interaction with apps. The consumer version of Google+ currently has low usage and engagement: 90 percent of Google+ user sessions are less than five seconds.
Our review showed that our Google+ APIs, and the associated controls for consumers, are challenging to develop and maintain. Underlining this, as part of our Project Strobe audit, we discovered a bug in one of the Google+ People APIs:
Users can grant access to their Profile data, and the public Profile information of their friends, to Google+ apps, via the API.
The bug meant that apps also had access to Profile fields that were shared with the user, but not marked as public.
This data is limited to static, optional Google+ Profile fields including name, email address, occupation, gender and age. (See the full list on our developer site.) It does not include any other data you may have posted or connected to Google+ or any other service, like Google+ posts, messages, Google account data, phone numbers or G Suite content.
We discovered and immediately patched this bug in March 2018. We believe it occurred after launch as a result of the API’s interaction with a subsequent Google+ code change.
We made Google+ with privacy in mind and therefore keep this API’s log data for only two weeks. That means we cannot confirm which users were impacted by this bug. However, we ran a detailed analysis over the two weeks prior to patching the bug, and from that analysis, the Profiles of up to 500,000 Google+ accounts were potentially affected. Our analysis showed that up to 438 applications may have used this API.
We found no evidence that any developer was aware of this bug, or abusing the API, and we found no evidence that any Profile data was misused.”
Update: In a new revelation from Wall Street Journal, “Google opted not to disclose to users its discovery of a bug that gave outside developers access to private data. It found no evidence of misuse.” Below is an image of how a software glitch allowed app developers to potentially access Google+ user data.
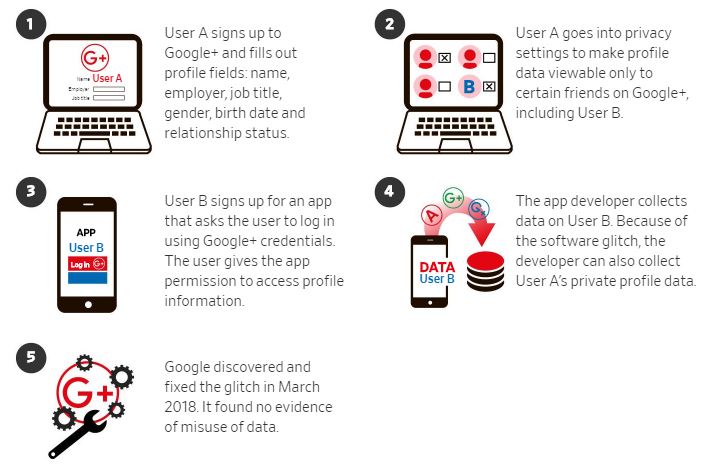
Source:People briefed on the incident and documents reviewed by The Wall Street Journal