Data breach exposed massive phishing and credit card fraud operation targeting 100,000s Facebook users in just 3 months

Every year, millions of people around the world fall victim to credit card fraud. The situation is not getting any better as hackers and scammers are now improving their tradecraft and tools by targeting victims on social media.
For hackers, the best social media platform with the largest digital footprint and attack surface is none other than Facebook. Recently, the research team at VPNMentor, a site that offers users helpful tools to navigate VPNs and web privacy, discovered an unsecured Elasticsearch server which exposed a scam targeting Facebook users, tricking them into providing login credentials for their private accounts. The incidents took place between June and September 2020. The hackers then used the stolen login credentials to hack Facebook accounts and post links directing people to their network of Bitcoin scam websites.
The VPNMentor research team discovered the scam via an unsecured database used by the fraudsters to store private data belonging to 100,000s of their victims. The people running the scam were tricking Facebook users into providing login credentials for their private accounts via a tool pretending to reveal who was visiting their profiles.
The fraudsters used the stolen login credentials to share spam comments on Facebook posts via the victims hacked account, directing people to their network of scam websites. These websites all eventually led to a fake Bitcoin trading platform used to scam people out of ‘deposits’ of at least €250.
It was a vast operation, spanning the entire globe. However, the fraudsters left the database used to harvest and store their victims’ details completely open for anyone to view and access. With this information, we were able to expose their operation.
According to VPNMentor team, “the day after they discovered the database, it was attacked by the ongoing widespread Meow cyberattack, which completely wiped all its data. The database went offline the same day and was no longer accessible. We believe the fraudsters did this following the Meow attack, but can’t confirm.”

After entering login credentials into the window – or any text for that matter – a fake loading page appeared promising to share the full list.
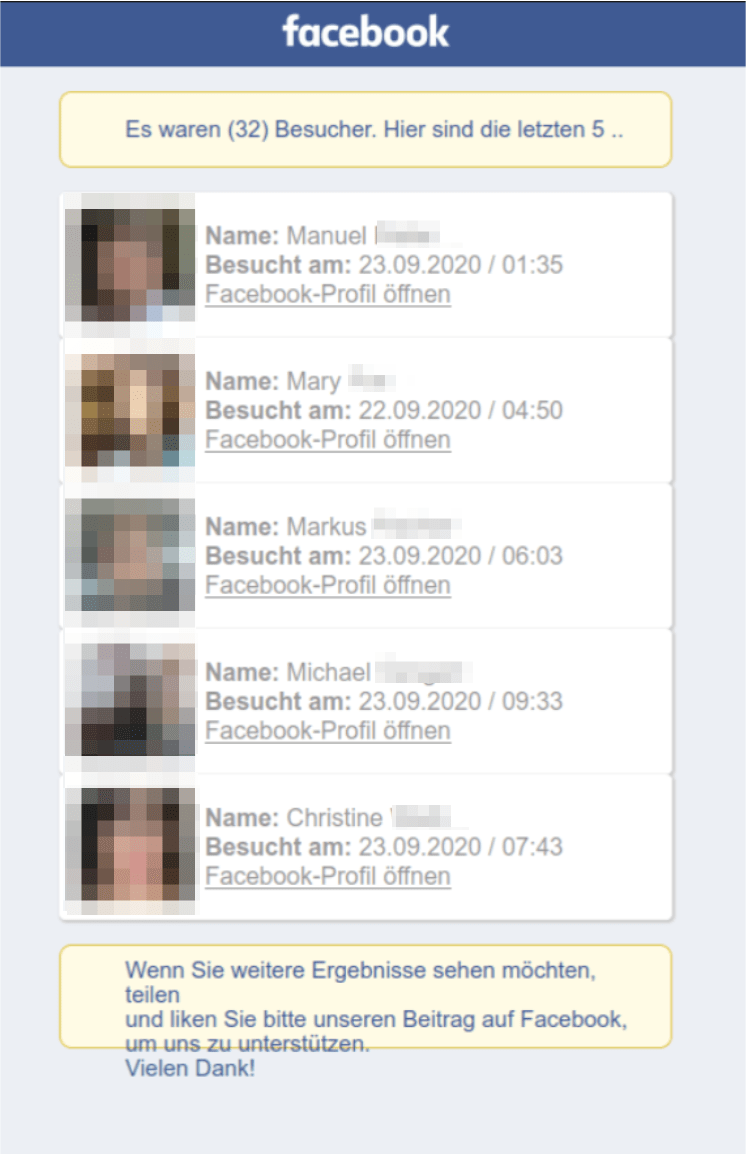
Finally, the victim was redirected to the Google Play page for an unrelated Facebook analytics app.
In the process, the fraudsters saved the victim’s Facebook username and password on the exposed database for future use in their other criminal activities. These were stored in Cleartext format, making it easy for anyone who found the database to view, download, and steal them.
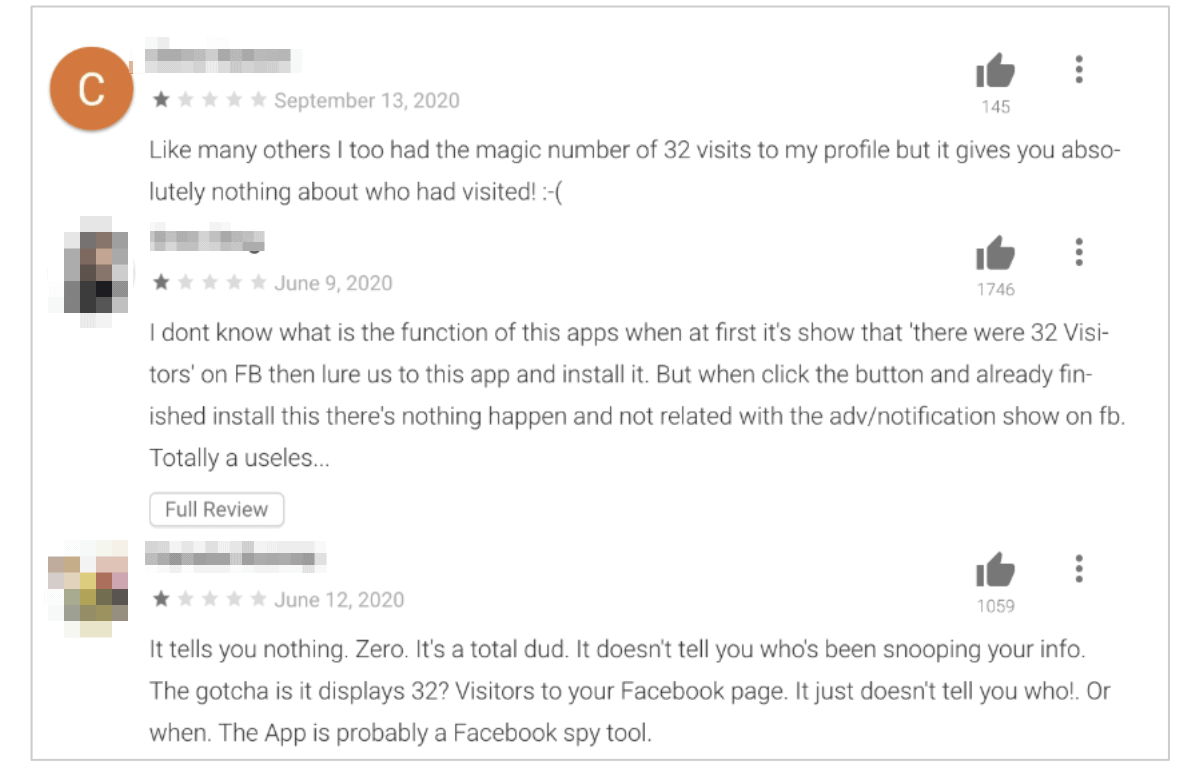
Negative feedback on the analytics app from victims of the fraud, expressing their dissatisfaction with a seemingly broken app, show numerous people have gone through the entire scam and unknowingly had their data stolen.
Their research also included Bitcoin and fake websites and scam domains.
The Bitcoin Scam
The next phase of the scam started once the fraudsters had their victims’ login credentials. They would take over accounts and comment on Facebook posts published in the victim’s network. The comments all contained links to a separate network of scam websites owned and operated by the fraudsters.
In this phase, the fraudsters hoped to direct people to a huge Bitcoin fraud scheme.
You can read the entire report here.




