Millions of Subarus exposed to remote unlocking and tracking due to security flaws, researchers find

Security researchers have uncovered significant vulnerabilities in Subaru’s Starlink system that could have allowed hackers to track vehicles’ locations over the past year and control certain features remotely. Although the flaws have been patched, the discovery raises serious concerns about privacy in connected vehicles and the access car companies grant employees to sensitive customer data.
It all started when security researcher Sam Curry bought his mother a Subaru. Curry, known for probing connected systems, made a deal with his mom: she’d let him hack the car at some point. Last November, he finally got around to testing the 2023 Subaru Impreza’s internet-connected features. With help from fellow researcher Shubham Shah, it didn’t take long to uncover weaknesses in Subaru’s web portal, according to Ars Technica, which cited Wired as the first to report the story.
The pair discovered vulnerabilities that allowed them to reassign control of the car’s Starlink features to any device of their choosing. They could unlock the car, honk its horn, and even start its ignition. Perhaps most concerning, they were able to access detailed location data for the entire year the car had been in use. This information revealed every place Curry’s mother had visited, down to specific parking spaces and personal stops like church and doctor’s offices.
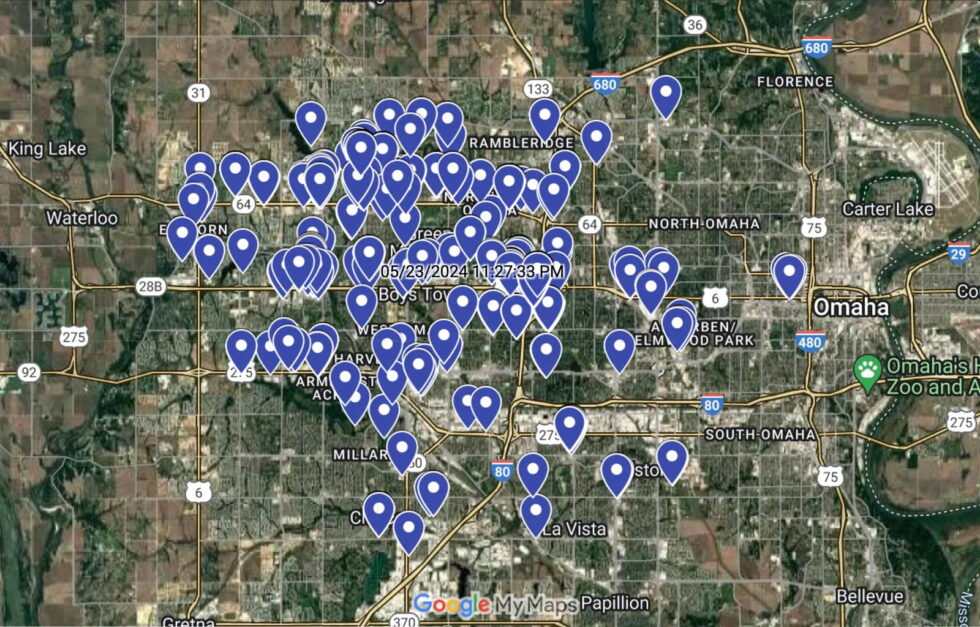
A year of location data for a 2023 Subaru Impreza, accessible through Subaru’s employee admin portal due to identified security vulnerabilities. Credit: Sam Curry
“You can retrieve at least a year’s worth of location history for the car, where it’s pinged precisely, sometimes multiple times a day,” Curry explained. “Whether somebody’s cheating on their wife or getting an abortion or part of some political group, there are a million scenarios where you could weaponize this against someone.”
Subaru Starlink Vulnerability Exposed Cars to Remote Hacking: Researchers Uncover Year-Long Tracking Vulnerability and Privacy Risks
Curry and Shah detailed their findings in a blog post published last week, revealing how vulnerabilities in a Subaru website designed for employees allowed them to reset an employee’s account credentials and access vehicle data. By exploiting these weaknesses, they could track any Subaru vehicle equipped with Starlink in the US, Canada, or Japan. The hack relied on a series of missteps: email-based password resets, security question answers validated in the browser, and overly broad employee access to customer data.
After being alerted in November, Subaru quickly addressed the flaws. The company stated, “After being notified by independent security researchers, [Subaru] discovered a vulnerability in its Starlink service that could potentially allow a third party to access Starlink accounts. The vulnerability was immediately closed and no customer information was ever accessed without authorization.”
Still, the incident highlights how much data automakers collect and who has access to it. Subaru confirmed that some employees can access historical location data, claiming this is necessary for cases like sharing vehicle locations with first responders after an accident. Curry, however, questioned the need for such extensive data retention.
“There’s an expectation that a Google employee isn’t going to just go through your emails in Gmail,” he said. “But there’s literally a button on Subaru’s admin panel that lets an employee view location history.”
Subaru’s situation isn’t isolated. The researchers’ work is part of a broader trend of exposing vulnerabilities in connected vehicles. Over the past two years, Curry and his colleagues have identified similar flaws in web systems used by Acura, Toyota, Hyundai, Kia, and several luxury brands. While many of these cases involved the potential for remote control of car functions, Subaru’s extensive collection of location data stands out.
This discovery adds to growing concerns over the automotive industry’s data practices. In September, the Mozilla Foundation called modern cars a “privacy nightmare,” reporting that 92% of automakers offer little to no control over data collection and 84% reserve the right to sell or share the data they collect. Subaru has denied selling location data.
The broader takeaway is that connected cars are increasingly becoming repositories of sensitive personal data. Curry’s findings underscore the need for better safeguards to protect drivers from potential abuses, both by hackers and by those with authorized access. As car companies expand their connected services, the balance between functionality and privacy remains a critical challenge.




