Microsoft’s Bing Chat is now infested with malware
On May 4, Microsoft released its GPT4-powered Bing Chat to the general public with great fanfare. However, it didn’t take long for malicious advertisements to infiltrate the AI-driven Bing Chat responses. These rogue ads promoted counterfeit download sites that distributed malware.
A recent report from MalwareBytes has uncovered the infiltration of ads promoting malware within Bing Chat responses. Notably, these malicious ads have been masquerading as download sites for the widely-used ‘Advanced IP Scanner’ utility, a tool previously associated with the activities of RomCom RAT and Somnia ransomware operators.
In a blog post, MalwareBytes shared how users seeking software downloads can be lured into visiting malicious websites and unknowingly installing malware through a Bing Chat conversation.
The researchers first discovered that when users asked Bing Chat for instructions on downloading Advanced IP Scanner, it would generate a chat response with a link to download the utility. However, upon hovering over an underlined link in the chat, Bing Chat sometimes displayed an advertisement first, followed by the genuine download link. In this particular scenario, the sponsored link turned out to be a malicious advertisement promoting malware.
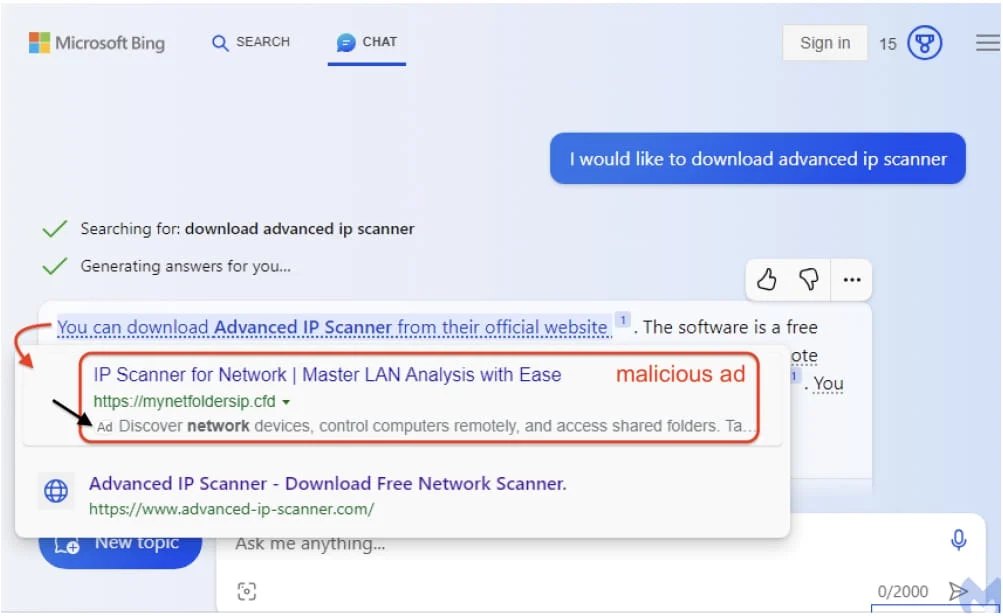
Users are then presented with the option to click on either of the two links, although the first link often receives more attention due to its prominent placement. Despite the presence of a small ‘Ad’ label next to this link, it could easily be overlooked, leading users to perceive it as a standard search result.
Phishing site serves malware
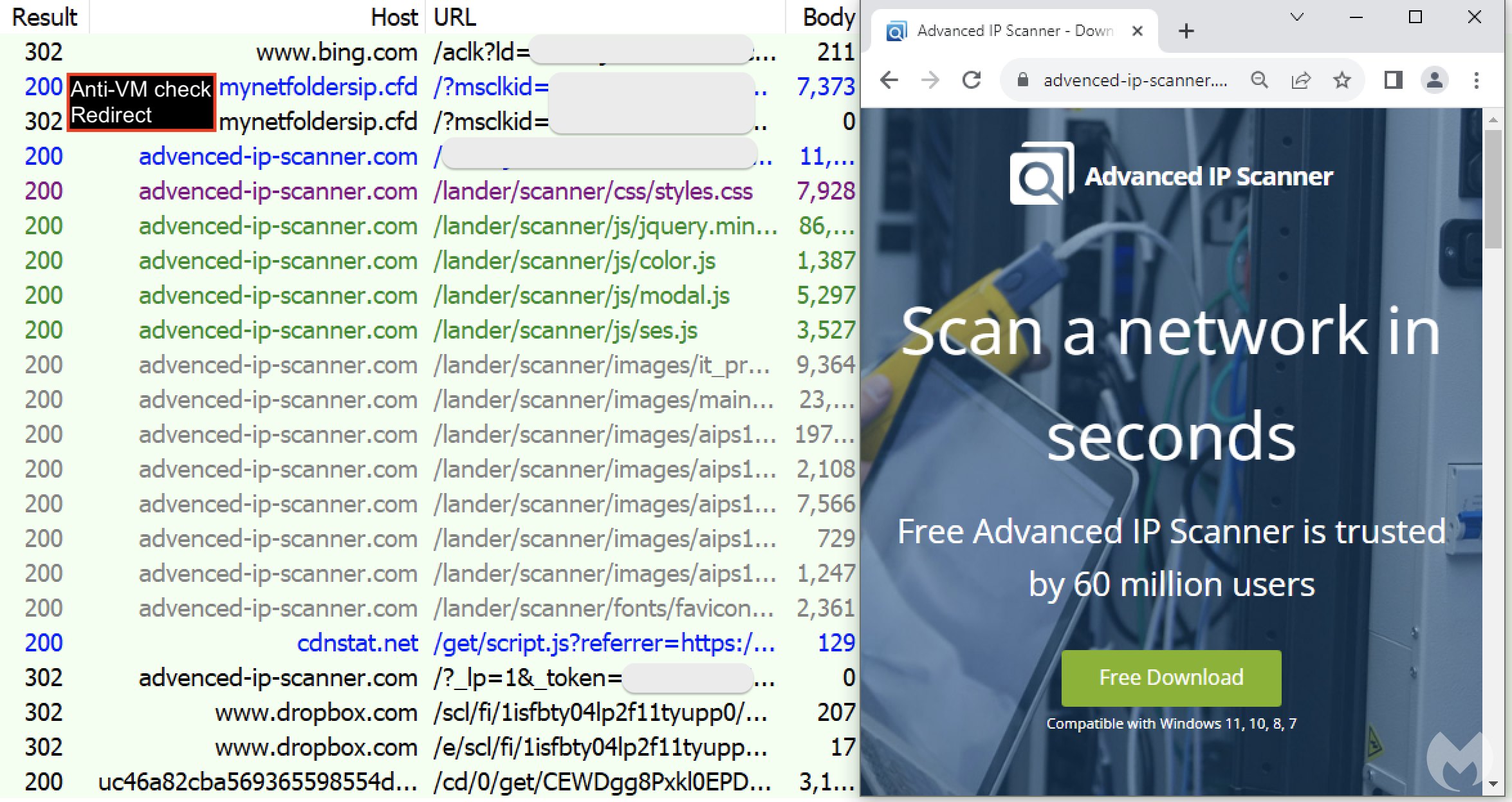
Upon clicking the first link, users are directed to a website (mynetfoldersip[.]cfd) designed to filter traffic and distinguish genuine victims from bots, sandboxes, or security researchers. This determination is made by examining factors like the user’s IP address, time zone, and various system settings, including web rendering characteristics that identify virtual machines.
If the user is confirmed to be a real human, they are redirected to a counterfeit site (advenced-ip-scanner[.]com) meticulously designed to mimic the official one. In contrast, those identified otherwise are directed to a diversionary page. Subsequently, victims are prompted to download what appears to be the legitimate installer and execute it.
How did Microsoft get here?
It all started in February 2023 when Microsoft unveiled Bing Chat, powered by OpenAI’s GPT-4 engine in a bid to challenge Google’s dominance in the search industry. The aim is to use Bing Chat to provide users with a more interactive and user-friendly search experience compared to the traditional search query and result format.
As part of its revenue strategy, Microsoft began incorporating ads into Bing Chat conversations in March. However, this move inadvertently created an opportunity for malicious actors who increasingly exploit search advertisements to distribute malware.
Moreover, engaging in conversations with AI-powered chat tools can foster an unwarranted sense of trust, potentially convincing users to click on ads. This level of trust differs from the usual skepticism applied when viewing impersonal search results.
The conversational nature of interactions with AI assistants can imbue AI-provided URLs with an unwarranted sense of authority and reliability. Consequently, the existing problem of malvertising in search platforms is exacerbated by the introduction of AI assistants.
While these ads are labeled as “promoted results” when users hover over a link in Bing Chat conversations, this measure may not be robust enough to mitigate the associated risks effectively.