This 55-year-old Latvian woman, mother of two, is a member of the Trickbot cybercrime gang responsible for infecting millions of computers around the world

No week goes by with another report of a ransomware attack. The growing threat of cyberattacks and malware has increased over the last decade. In 2021, ransomware attacks on Colonial Pipeline, JBS Foods, and other major organizations dominated the headlines. The attacks continue in 2022 with show no sign of slowing down.
So far this year, there were dozens of malware attacks on private companies and governments. Just this morning, the Lockbit 2.0 ransomware gang announced it hacked France’s Ministry of Justice’s systems and threatened to release the files stolen unless France government meets its demands.
According to Statista, the vast majority of malware attacks worldwide in 2021 took place in North America, with the number of automated bot-attacks far exceeding that of those executed by humans. Of all the malware attacks, ransomware has become the most popular form of attack in recent years growing 350% in 2018. The average ransomware payment by businesses in 2021 increased by 82% year over year to $570,000. The largest ransom demand observed so far in 2021 was $100 million.
You may be wondering, who is behind these malware attacks and what are their motives? Of course, we may know exactly who and how many hacker groups are behind all the global cyberattacks. What we do know is that some of these attacks are caused by state-sponsored threat actors.
In 2021, MosaicLoader malware was reportedly responsible for nearly 70% of all malicious infections that occur online. The malware is so dangerous that it can collect details about your online banking information, your credit card numbers, etc. The virus can even record everything you type with your keyboard and then send it back to the hackers.
According to ZDNet, citing the eSentire Ransomware Report, just six ransomware cybercrime gangs are responsible for breaching the cybersecurity defenses of 292 organizations in 2021. The report estimated that the hacker groups managed to bring in at least $45 million from these attacks and also provided details of multiple incidents that were never reported.
However, one hacker group that may be unknown to many is a cybercrime gang out of Eastern Europe. Known as Trickbot Group, this criminal organization is a malware-as-a-service platform that operated in Russia, Belarus, Ukraine, and Suriname. The group is said to be responsible for infecting millions of computers and seeding many of those systems with ransomware.
Last year, the US Department of Justice (DOJ) announced the arrest of a 55-year-old Latvian woman who goes by the name Alla “Max” Witte. The DOJ alleged that the self-employed website designer and mother of two worked as a programmer for Trickbot.
According to the indictment, Alla Witte, aka Max, 55, was charged in 19 counts of a 47-count indictment. The agency alleged that Alla Witte had worked as a programmer and accuses her of participating in a criminal organization referred to as the “Trickbot Group,” which deployed the Trickbot malware.
The Trickbot Group primarily targeted victim computers belonging to businesses, entities, and individuals, including those in the Northern District of Ohio and elsewhere in the United States. Targets included hospitals, schools, public utilities, and governments. Witte, who previously resided in Paramaribo, Suriname, was arrested on Feb. 6, in Miami, Florida.
So, the question everyone was asking is, just how did a self-employed website designer and mother of two come to work for one of the world’s most notorious cybercriminal groups and then leave such a digital trail of clues indicating her involvement with the gang?
A piece written by KrebsonSecurity, the indictment released by the DOJ (PDF) provides some clues about Alla “Max” Witte’s technical background. The 61-page indictment says that “Witte provided code to the Trickbot Group for a web panel used to access victim data stored in a database.”
On page 13 of the indictment, DOJ said that “Witte was a Malware Developer for the Trickbot Group, overseeing the creation of code related to the monitoring and tracking of authorized users of the Trickbot malware, the control and deployment of ransomware, obtaining payments from ransomware victims, and developing tools and protocols for the storage of credentials stolen and exfiltrated from victims infected by Trickbot.”
The DOJ also revealed that that database contained a large number of credit card numbers and stolen credentials from the Trickbot botnet, as well as information about infected machines available as bots.
The indictment further reveals that:
“Witte provided code to this repository that showed an infected computer or ‘bot’ status in different colors based on the colors of a traffic light and allowed other Trickbot Group members to know when their co-conspirators were working on a particular infected machine.”
Witte was a national of Russia. During the timeframe of the indictment, Witte resided in Suriname. She was arrested in Miami while flying from Suriname.
In addition to the DOJ indictment, KrebsonSecurity also cited a tweet posted by Vitali Kremez. The tweet seems to indicate at one point last year, Witte actually hosted Trickbot malware on a vanity website registered in her name — allawitte[.]nl.
That’s not all. A screengrab from the archive page of allawitte[.]nl in 2016 also shed more light on who Witte really is.
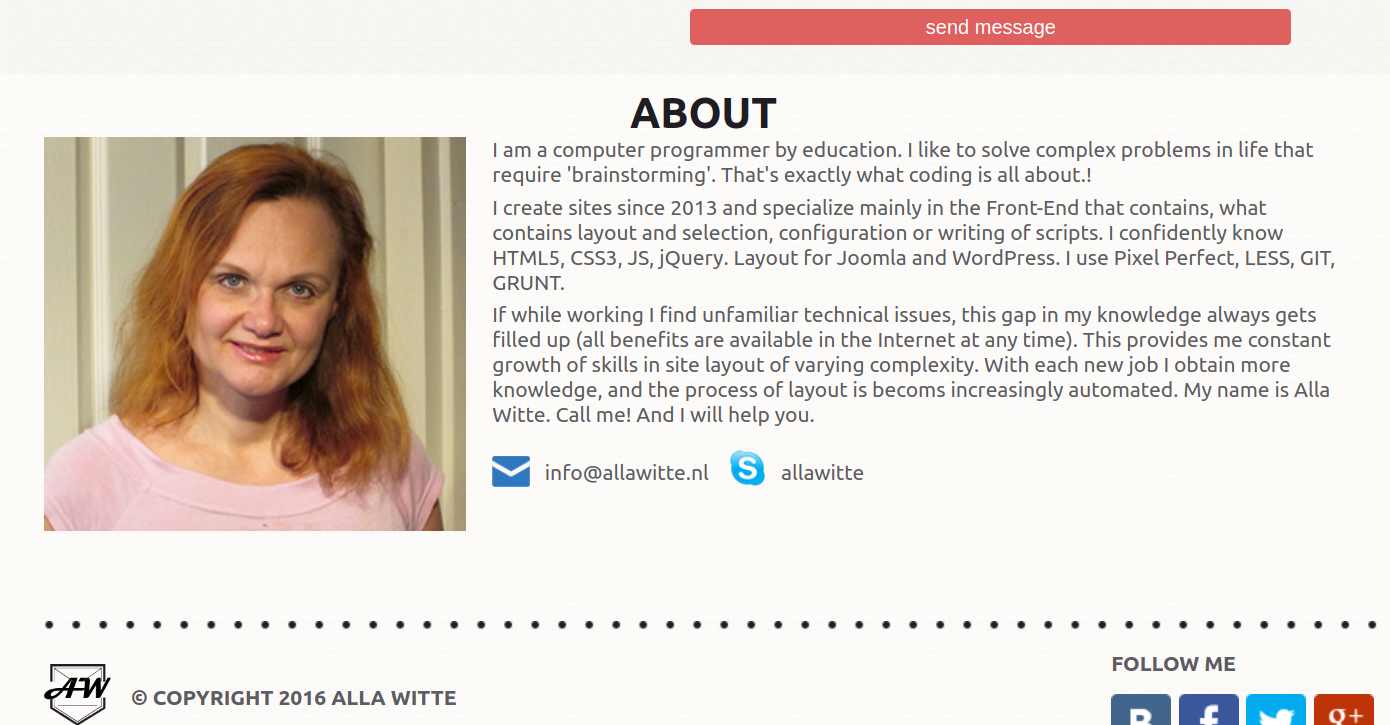
Credit: KrebsOnSecurity
Besides, another archive from a Google-translated post that Witte made to her Vkontakte page on April 22, 2013, five years before allegedly joining the Trickbot group, reveals that Witte loved to fly to clients in different countries.
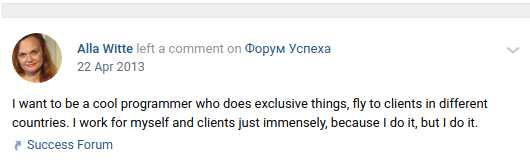
Credit: KrebsOnSecurity
Meanwhile, DOJ Deputy Attorney General Lisa O. Monaco said: “This indictment demonstrates the broad reach of the Department of Justice’s Ransomware and Digital Extortion Task Force.”
She added: “Trickbot infected millions of victim computers worldwide and was used to harvest banking credentials and deliver ransomware. The defendant is accused of working with others in the transnational criminal organization to develop and deploy a digital suite of malware tools used to target businesses and individuals all over the world for theft and ransom. These charges serve as a warning to would-be cybercriminals that the Department of Justice, through the Ransomware and Digital Extortion Task Force and alongside our partners, will use all the tools at our disposal to disrupt the cybercriminal ecosystem.”
“The Trickbot malware was designed to steal the personal and financial information of millions of people around the world, thereby causing extensive financial harm and inflicting significant damage to critical infrastructure within the United States and abroad,” said Acting U.S. Attorney Bridget M. Brennan of the Northern District of Ohio. “Federal law enforcement, along with assistance provided by international partners, continue to fight and disrupt ransomware and malware where feasible. We are united in our efforts to hold transnational hackers accountable for their actions.”
“Witte and her associates are accused of infecting tens of millions of computers worldwide, in an effort to steal financial information to ultimately siphon off millions of dollars through compromised computer systems,” said Special Agent in Charge Eric B. Smith of the FBI’s Cleveland Field Office. “Cyber intrusions and malware infections take significant time, expertise, and investigative effort, but the FBI will ensure these hackers are held accountable, no matter where they reside or how anonymous they think they are.”




