Hackers stole $15 million from 150 companies by impersonating email addresses of senior executives using Microsoft Office 365 cloud

Cybercriminals and hackers stole $15 million from 150 companies in what’s known to be one of the largest BEC attacks. Business email compromise (BEC)—also known as email account compromise (EAC) is a method where cybercriminals or hackers send an email message that appears to come from a known source making a legitimate request.
In a series of attacks which were first discovered by an Israeli cybersecurity startup Mitiga, between April and September, cybercriminals stole as much as $15 million by impersonating senior executives at as many as 150 companies using what appear to be legitimate Microsoft Office 365 email addresses in a bid to make their attacks more successful. Mitiga said it has notified the FBI, the Secret Service, and Microsoft.
“We believe that the threat actor chose to use Office 365 in order to improve the likelihood of a successful attack, thanks to the credibility it can generate,” the company wrote in a report released Wednesday. “The threat actor’s use of the same technology stack reduced both suspicious discrepancies and the likelihood of triggering malicious detection filtering, which ultimately contributed to the rogue emails slipping through.”
According to Mitiga, as part of the campaign, the attackers used rogue domains registered on Wild West Domains (which is owned by GoDaddy), all of which mimicked the websites of legitimate businesses. In one incident, which also resulted in a multi-million-dollar global transaction, Mitiga found that the “threat actor’s attack extended over several months,” that it was carefully prepared, and that it also involved the “monitoring and manipulation of email traffic before and during the transfer of funds.”
After looking into that attack, Mitiga discovered a significant number of other, possibly-linked BEC frauds that have been perpetrated by the same group. They used 15 different Office 365 accounts to register 150 additional domains, all of them registered on Wild West Domains and designed to imitate other legitimate businesses, Mitiga said.
It’s a classic but hugely successful case of what’s known as business email compromise (BEC) fraud where crooks impersonate company partners and convince them to send money to their bank accounts. For instance, the hacker will set up email server domains so they could be mistaken for a real business, such as forb3s.com rather than forbes.com. Mitiga said that in one case it investigated, a hacker had learned of a target’s wire transfer by somehow gaining access to an employee’s Office 365 email account. Then, just as the money was about to be sent by the unnamed victim organization, the fraudster impersonated the recipient and sent new wire instructions so they received the money rather than the legitimate seller. The latter never received the money they were due.
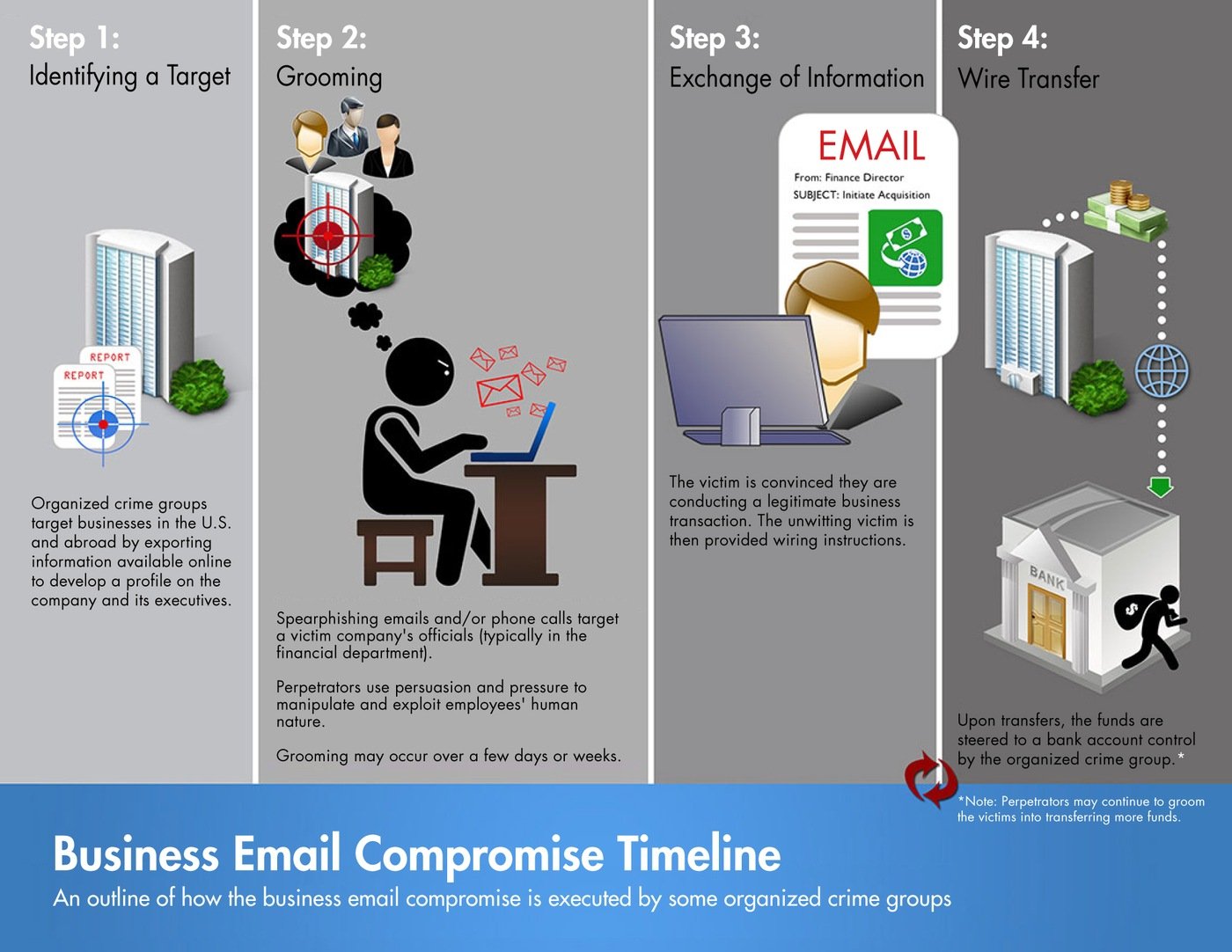
Below is how the BEC attack works. A scammer might:
- Spoof an email account or website. Slight variations on legitimate addresses (john.kelly@examplecompany.com vs. john.kelley@examplecompany.com) fool victims into thinking fake accounts are authentic.
- Send spearphishing emails. These messages look like they’re from a trusted sender to trick victims into revealing confidential information. That information lets criminals access company accounts, calendars, and data that gives them the details they need to carry out the BEC schemes.
- Use malware. Malicious software can infiltrate company networks and gain access to legitimate email threads about billing and invoices. That information is used to time requests or sends messages so accountants or financial officers don’t question payment requests. Malware also lets criminals gain undetected access to a victim’s data, including passwords and financial account information.
Credit: FBI
How to Protect Yourself
- Be careful with what information you share online or on social media. By openly sharing things like pet names, schools you attended, links to family members, and your birthday, you can give a scammer all the information they need to guess your password or answer your security questions.
- Don’t click on anything in an unsolicited email or text message asking you to update or verify account information. Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.
- Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
- Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
- Set up two-factor (or multi-factor) authentication on any account that allows it, and never disable it.
- Verify payment and purchase requests in person if possible or by calling the person to make sure it is legitimate. You should verify any change in an account number or payment procedures with the person making the request.
- Be especially wary if the requestor is pressing you to act quickly.




